
DMARC (Domain-based Message Authentication, Reporting, and Conformance) works with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to authenticate mail senders. This is just one additional tool in the never-ending fight against phishing and spoofing. DMARC also instructs receiving servers on how to proceed when incoming emails fail SPF or DKIM validation.
Before you can enable DMARC, you first need to have properly configured SPF and DKIM.
Configure SPF
Microsoft guides you in creating an SPF TXT Domain record when you first add your custom domain to Office 365 so you should already have that set up. You can verify this in the Office 365 admin centre:

Configure DKIM
- Microsoft 365 admin centre > Security > Policies & rules > Threat Policies > Email authentication settings > DKIM.
- Select your domain and try to enable DKIM.
- This will initially fail, but will show a message explaining what DNS records you need to add for the domain in question.
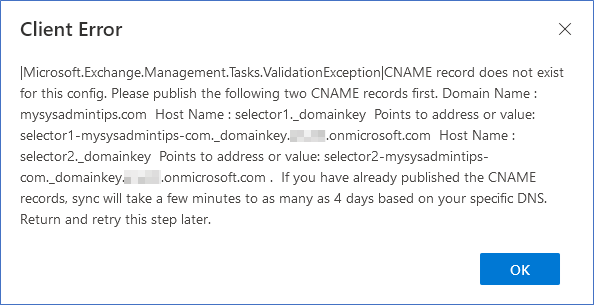
- Add the DNS records as per the message above.
- CNAME Record 1:
- Name: selector1._domainkey
- Value: selector1-yourdomain-com._domainkey.initial_office365_domain.onmicrosoft.com
- CNAME Record 2:
- Name: selector2._domainkey
- Value: selector2-yourdomain-com._domainkey.initial_office365_domain.onmicrosoft.com
- CNAME Record 1:
- Give it some time for DNS to update (normally a few minutes, but it can take much longer in some instances) and enable DKIM again. This time it should succeed.
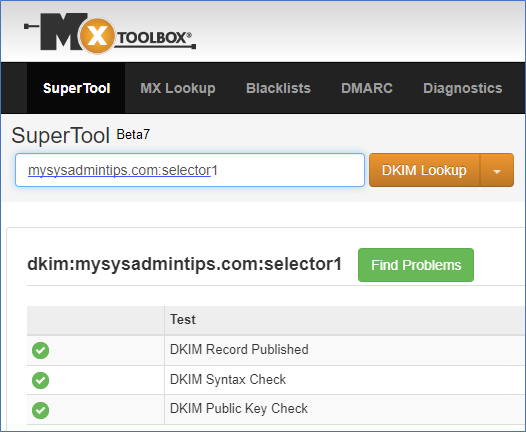
- Use MX Toolbox to verify that the DKIM configuration is valid.
Configure DMARC
- Create the following TXT domain record for your domain.
- Name: _dmarc
- Value: v=DMARC1; p=none; pct=100; rua= mailto:email-logs@your-domain.com; ruf=mailto:email-logs@your-domain.com; fo=1
- Modify the value per your requirements:
- p – policy that instructs the receiving email server what to do with emails that fail DMARC checks. You can set the policy to none, quarantine, or reject. In this instance, we set the policy to none so we can evaluate the setup and review reporting before changing it to quarantine or reject.
- pct – the percentage of email affected by the DMARC. In this case 100%.
- rua – email address to send aggregate reports of emails failing DMARC. These are sent by the receiving server, normally once a day. No personally identifiable information is included.
- ruf – email address to send forensic reports of emails failing DMARC. These are sent in real-time by the receiving server for each failed message. It May contain personally identifiable information. Not all email servers send these types of reports.
- fo – failure reporting level. 0 – report is sent when both SPF and DKIM fail. 1 – the report is sent when either SPF or DKIM fails.
- Note: If you are sending DMARC reports to a different domain, the receiving domain must have a DNS TXT record in the format:
- Name: *._report._dmarc
* here specifies wildcard, which means the domain will accept DMARC reports for any other domain. You can replace * with a specific domain if you wish. - Value: v=DMARC1
- Name: *._report._dmarc
- Use MX Toolbox to verify that the DMARC configuration is valid.
- Another good tool to help you understand and verify DMARC is https://www.learndmarc.com/
October 2023
Microsoft Office 365 Exchange
DMRC
DKIM
SPF

Leave a Reply