Received a somewhat worrying email from Google this morning:
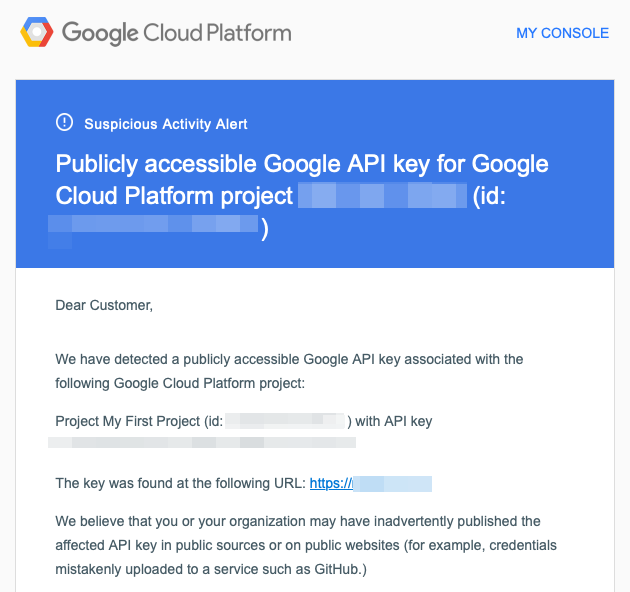
Full email text:
Suspicious Activity Alert
Publicly accessible Google API key for Google Cloud Platform project <project-name> (id: <project-id>)
Dear Customer,
We have detected a publicly accessible Google API key associated with the following Google Cloud Platform project:
Project <project-name> (id: <project-id>) with API key <api-key>
The key was found at the following URL: https://website-address.com
We believe that you or your organization may have inadvertently published the affected API key in public sources or on public websites (for example, credentials mistakenly uploaded to a service such as GitHub.)
Please note that as the project/account owner, you are responsible for securing your keys. Therefore, we recommend that you take the following steps to remedy this situation:
- If this key is intended to be public (or if a publicly accessible key isn’t preventable):
- Log in to the Google Cloud Console and review the API and billing activity on your account, ensuring the usage is in line with what you expected.
- Add API key restrictions to your API key, if applicable.
- If this key was NOT meant to be public:
- Regenerate the compromised API key: Search for Credentials in the cloud console platform, Edit the leaked key, and use the Regenerate Key button to rotate the key. For more details, review the instructions on handling compromised GCP credentials.
- Take immediate steps to ensure that your API key(s) are not embedded in public source code systems, stored in download directories, or unintentionally shared in other ways.
- Add API key restrictions to your API key, if applicable.
The security of your Google Cloud Platform account(s) is important to us.
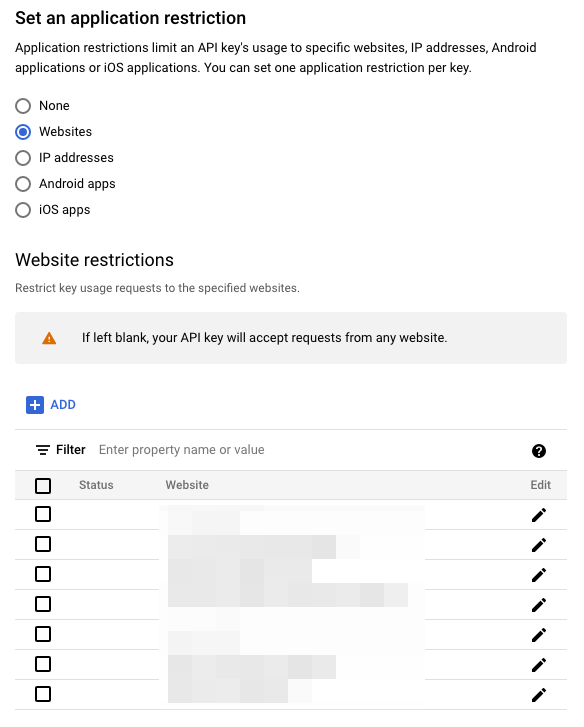
The key in question is a Google Maps API key that is supposed to be passed via javascript when using Google Maps API, so it will always be visible in the website source. The key is also restricted in the Google Cloud Console to specific websites/domains.
It seems that in this case Google went slightly overboard and sent those emails to all Google Cloud project owners where API keys are visible publicly, not taking into account whether they should be public or not and whether they are properly secured or not.
If you got such an email for your Google Maps API key, double-check that the key in question is restricted to specific domains in your Google Cloud Console.
March 2023
Google Cloud Console
Google Maps API Key


